How hackers use idle scans in port scan attacks
Por um escritor misterioso
Last updated 15 novembro 2024
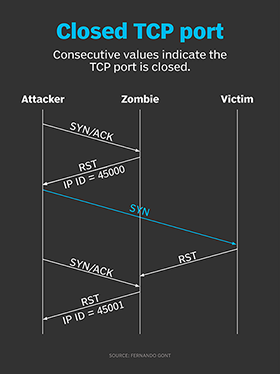
Hackers employ a variety of port scan attacks to gain entry into an enterprise network. Idle scans are a popular method to mask the hacker
Hackers exploit port scan attacks to mask their identities before launching an attack. One of their favorites: the idle scan.
Hackers exploit port scan attacks to mask their identities before launching an attack. One of their favorites: the idle scan.

Port Scanning - an overview

What is a Port Scanner and How Does it Work?
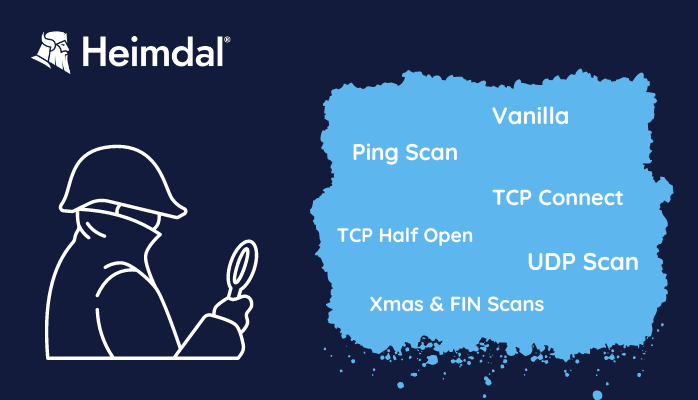
What Is a Port Scan Attack? Definition and Prevention Measures for Enterprises
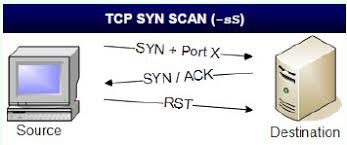
SYN Stealth, XMAS, NULL, IDLE, FIN

NMap > Penetration Testing and Network Defense: Performing Host Reconnaissance

Legal Issues Nmap Network Scanning

How hackers use idle scans in port scan attacks
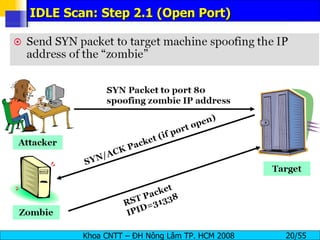
Module 3 Scanning
IDLE scan executing process Download Scientific Diagram
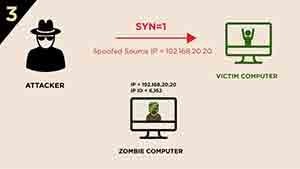
What is Idle Scan? ICterra Information and Communication Technologies
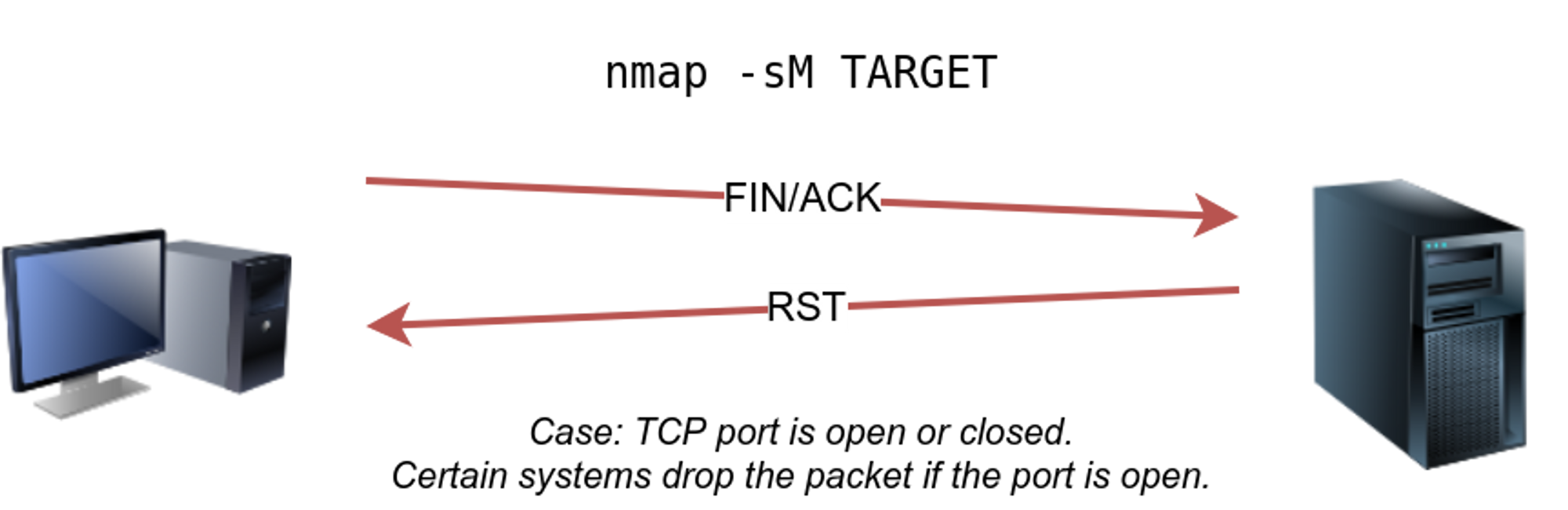
The Ultimate Guide to Port Scanning using Nmap
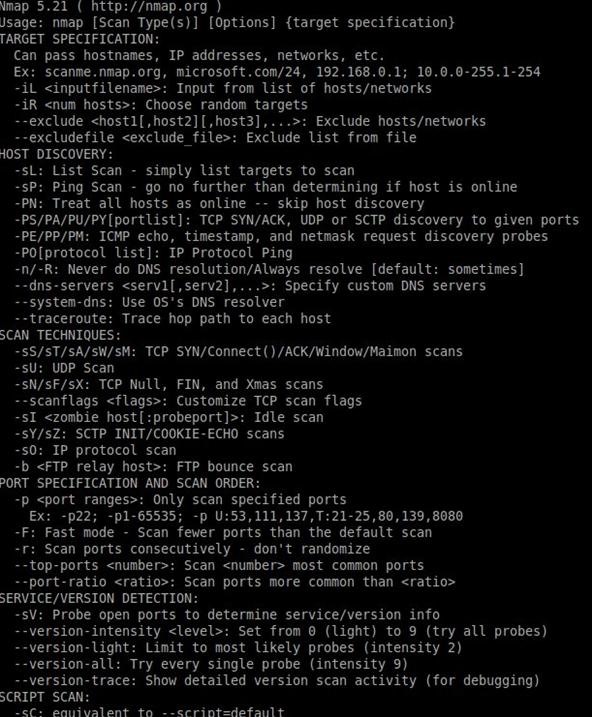
Hacking Reconnaissance: Finding Vulnerabilities in Your Target Using Nmap « Null Byte :: WonderHowTo

Performing an Idle Zombie Scan Nmap

Port Scanning - an overview
What Is Nmap? A Comprehensive Tutorial For Network Mapping
Recomendado para você
-
 IPChicken, Woo hoo! Lightspeed!, Richard De Guzman15 novembro 2024
IPChicken, Woo hoo! Lightspeed!, Richard De Guzman15 novembro 2024 -
 The Fuck you Tony P Guide to getting around an IP ban!15 novembro 2024
The Fuck you Tony P Guide to getting around an IP ban!15 novembro 2024 -
 IP Chicken - Served Fresh Daily15 novembro 2024
IP Chicken - Served Fresh Daily15 novembro 2024 -
 How to Find Your Phone's IP Address on Android or iPhone15 novembro 2024
How to Find Your Phone's IP Address on Android or iPhone15 novembro 2024 -
 like ip chicken 🐔🐔🐔 Ip chicken, Smart city, Coding15 novembro 2024
like ip chicken 🐔🐔🐔 Ip chicken, Smart city, Coding15 novembro 2024 -
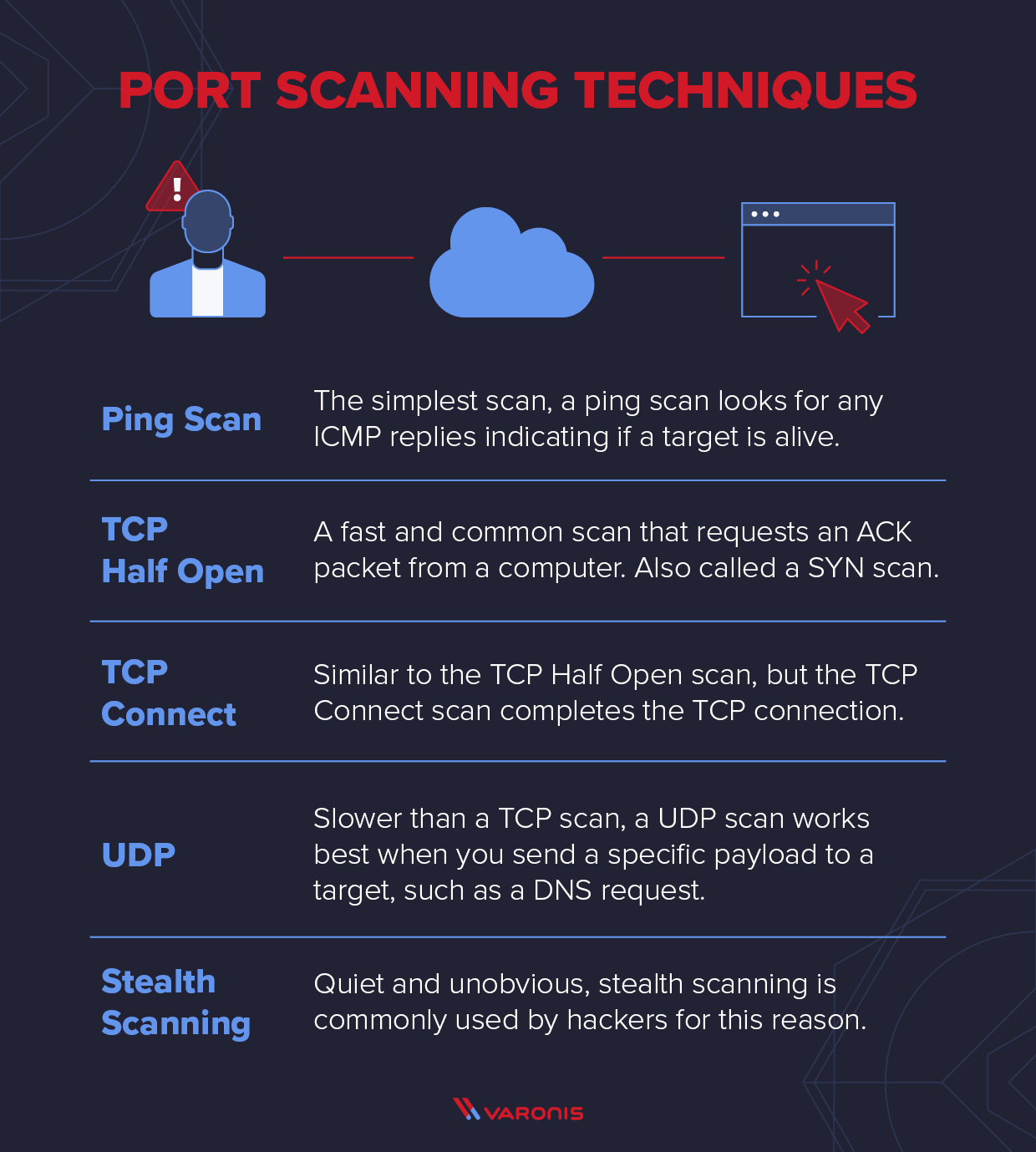 Explaining Port Scanning. A port scan is a common technique…, by Arth Awasthi15 novembro 2024
Explaining Port Scanning. A port scan is a common technique…, by Arth Awasthi15 novembro 2024 -
 How to Prevent Port Scan Attacks? - GeeksforGeeks15 novembro 2024
How to Prevent Port Scan Attacks? - GeeksforGeeks15 novembro 2024 -
Ethical Hacking With Net15 novembro 2024
-
 Malware analysis Malicious activity15 novembro 2024
Malware analysis Malicious activity15 novembro 2024 -
 iOS 15: Hide IP address in Safari15 novembro 2024
iOS 15: Hide IP address in Safari15 novembro 2024
você pode gostar
-
 Actor Casey Affleck and his girlfriend, Caylee Cowan, pose15 novembro 2024
Actor Casey Affleck and his girlfriend, Caylee Cowan, pose15 novembro 2024 -
 Sketch of Uzumaki Naruto. : r/Naruto15 novembro 2024
Sketch of Uzumaki Naruto. : r/Naruto15 novembro 2024 -
 The Two Female My Hero Academia Characters Who Were Originally Going To Be Male15 novembro 2024
The Two Female My Hero Academia Characters Who Were Originally Going To Be Male15 novembro 2024 -
 PlayStation Now vs. Xbox Games Pass – price, perks, device comparison - Millenium15 novembro 2024
PlayStation Now vs. Xbox Games Pass – price, perks, device comparison - Millenium15 novembro 2024 -
 Secador De Cabelo Gama Bella Tourmaline 3D Therapy Íons 2100W - lojaskubbo15 novembro 2024
Secador De Cabelo Gama Bella Tourmaline 3D Therapy Íons 2100W - lojaskubbo15 novembro 2024 -
 How To Download & Play Mobile Legends: Adventure On PC (202315 novembro 2024
How To Download & Play Mobile Legends: Adventure On PC (202315 novembro 2024 -
Andrea Bocelli - With my son Amos, ABF board member, at Global #TeacherPrize Andrea Bocelli Foundation Global Teacher Prize15 novembro 2024
-
Doentes por Futebol - Mais resultados dos jogos da Europa League de hoje. Estes foram os que aconteceram às 16h.15 novembro 2024
-
 Brookhaven Roblox Account15 novembro 2024
Brookhaven Roblox Account15 novembro 2024 -
 Kawaii Sketchbook: Cute anime girl blank drawing pad, manga artist notebook, doodle journal15 novembro 2024
Kawaii Sketchbook: Cute anime girl blank drawing pad, manga artist notebook, doodle journal15 novembro 2024


