Google Vulnerability Rewards Program, XSS, Best Practices
Por um escritor misterioso
Last updated 16 novembro 2024
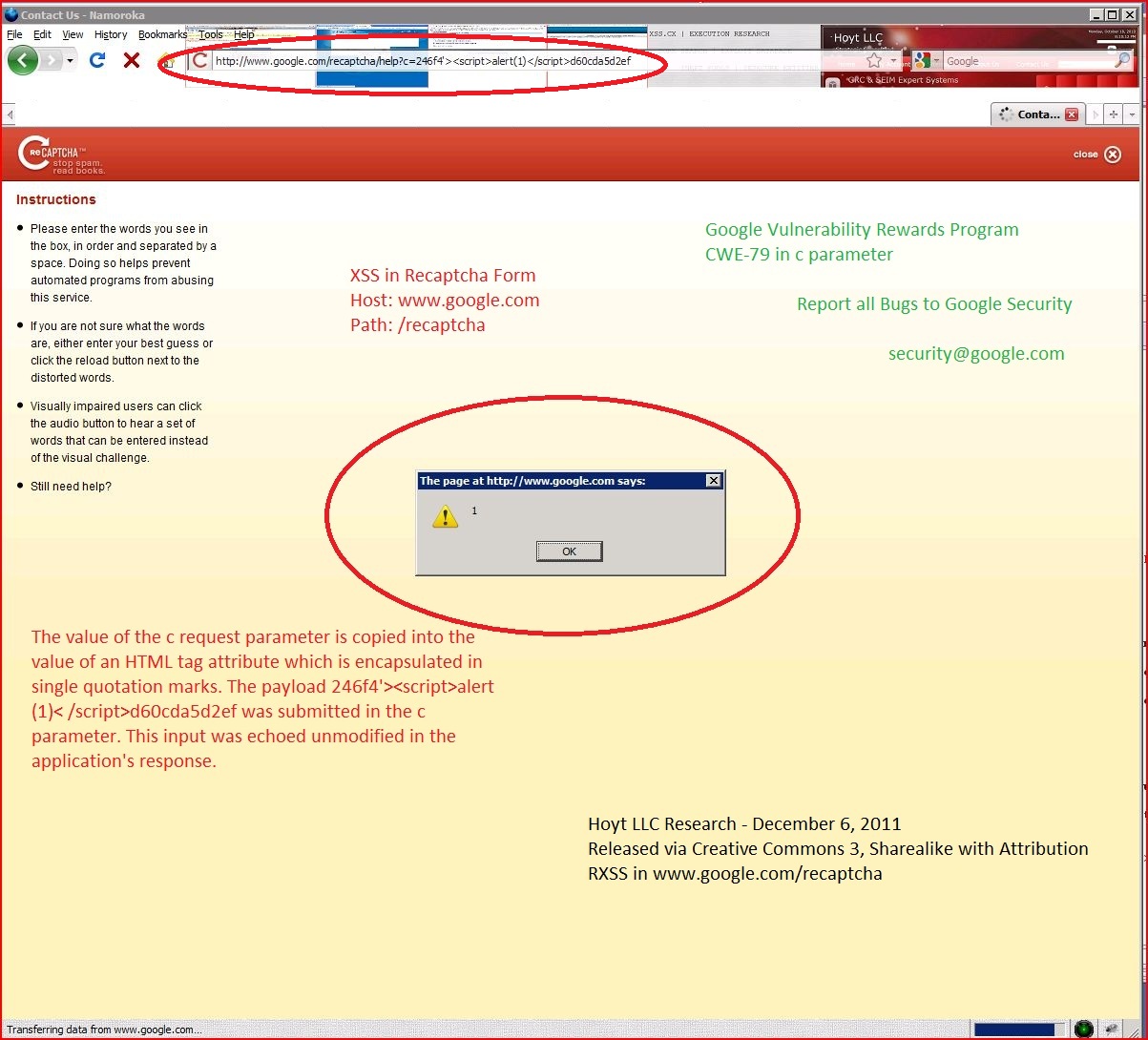
Phishing, Insecure Configuration, XSS, Cross Site Scripting, Best Practices, Vulnerability Management, Captcha Form, vulnerability rewards program, google.com, CWE-79, CAPEC-86, DORK, GHDB Report by

Part 5 — A Comprehensive Guide to Running a Bug Bounty Program, by Julian Berton

Newsletter Archive Archives - API Security News
Applied Sciences, Free Full-Text
XSS: Principles, Attacks and Security Best Practices

Google Online Security Blog: Vulnerability Reward Program: 2017 Year in Review

VIEH Group blogs
The fascinating World of Bug Bounty hunting - What it is and how you could get your feet wet

The process of reflected XSS Attack
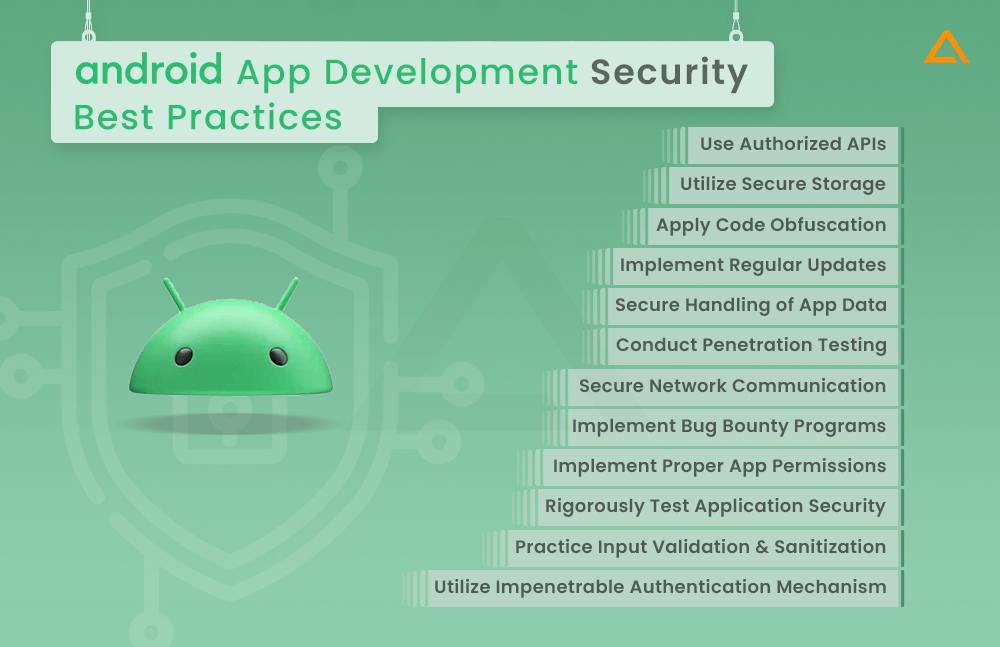
12 Android App Development Security Best Practices

XSS vulnerability uncovered in Google Voice browser extension

Top 5 Red Flags of Bug Bounty Program
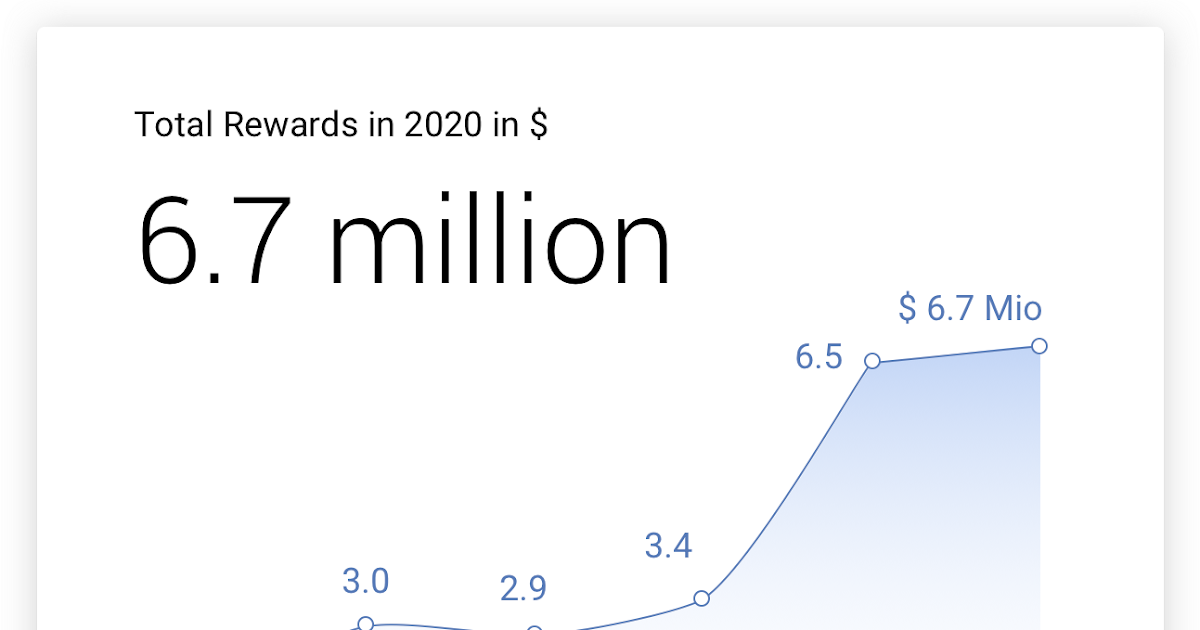
Google Online Security Blog: Vulnerability Reward Program: 2020 Year in Review

Google's Bug Bounty Hits $12 Million: What About the Risks?

12 Android App Development Security Best Practices
Recomendado para você
-
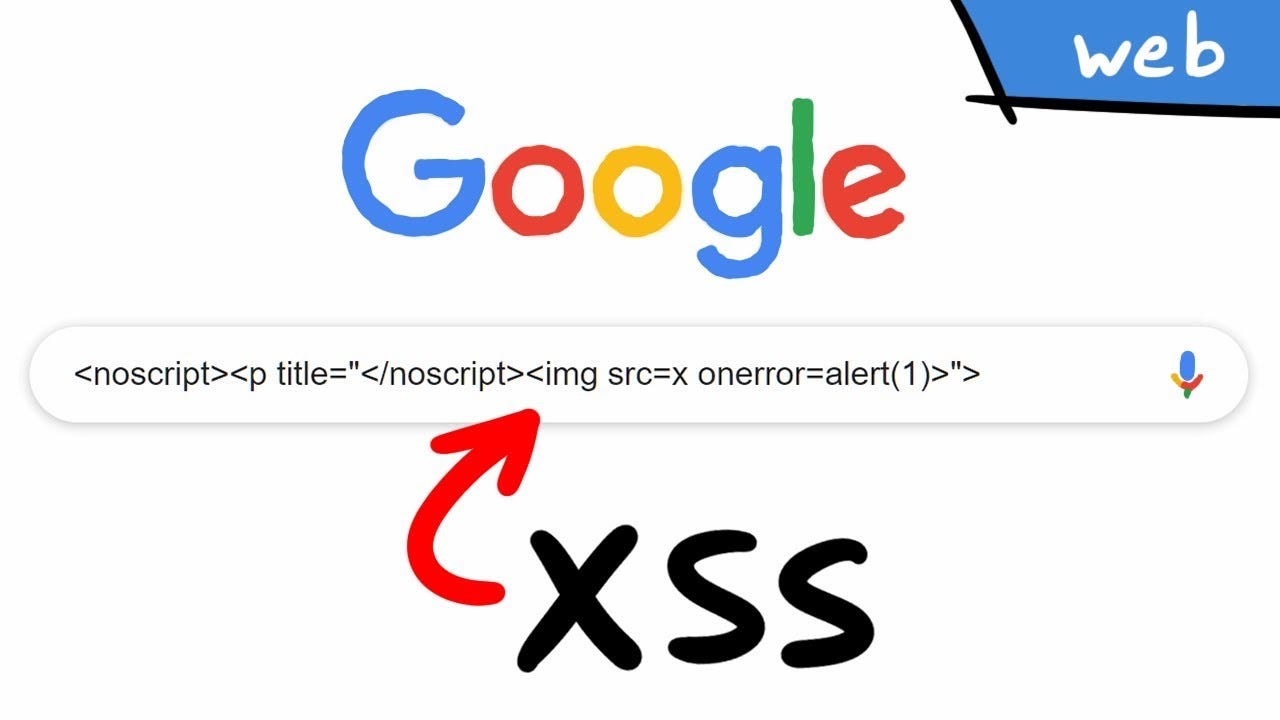 Cross Site Scripting ( XSS ) Vulnerability Payload List16 novembro 2024
Cross Site Scripting ( XSS ) Vulnerability Payload List16 novembro 2024 -
 What is XSS?, Understanding Cross-Site Scripting16 novembro 2024
What is XSS?, Understanding Cross-Site Scripting16 novembro 2024 -
 Defending Node Applications from SQL Injection, XSS, & CSRF16 novembro 2024
Defending Node Applications from SQL Injection, XSS, & CSRF16 novembro 2024 -
 BUG BOUNTY TIPS: ALTERNATE WAY TO FIND BLIND XSS16 novembro 2024
BUG BOUNTY TIPS: ALTERNATE WAY TO FIND BLIND XSS16 novembro 2024 -
 Cross Site Scripting Scanning - XSSS16 novembro 2024
Cross Site Scripting Scanning - XSSS16 novembro 2024 -
 DC Tonik Men's Skateboard Shoes - Grey/Grey/Grey XSSS16 novembro 2024
DC Tonik Men's Skateboard Shoes - Grey/Grey/Grey XSSS16 novembro 2024 -
 XSS exploitation without using the
XSS exploitation without using the